Many persons could have found out about it, yet no one has encountered it. Your cell phone conveys practically everything significant in your life—access to your web-based entertainment accounts, financial balances, subtleties, and significantly more. The last thing that you would need is for somebody to hack with phone and take the entirety of your data.
- Can Someone Hack into Your Phone By Calling You?
- How Does Someone Hack My Phone Remotely?
- Method 1. With a Spyware
- Method 2. SIM swap attack
- Method 3. Phishing emails
- Method 4. Public Wi-Fi networks
- How to Know If Your Phone is Hacked?
- What Can you Do When the Phone is Hacked?
- FAQs and Conclusion
Can Someone Hack into Your Phone By Calling You?
No. A hacker can call you, professing to be somebody official, thus getting sufficiently close to your subtleties. A phone is an individual device, including each indispensable piece of your life. Because of the quickly developing populace and the cutting-edge innovation, nearly everybody gangs a phone.
- Tragically, this device has the most significant potential to uncover the most delicate data to hackers. It is generally vital to guarantee you shield your phone from cheats and information snatchers.
- A hacker will probably not get to a phone simply by calling its owner. Be that as it may, hackers now and again take on the appearance of power figures. They might call somebody and request individual data, which is utilized to get to the proprietor's phone alongside different gadgets.
How Does Someone Hack My Phone Remotely?
It's anything but mysterious that hackers don't have to have your phone in their grasp to take your data. They can focus on any information put away there from a distance. Passwords, financial balance subtleties, instant messages, and photographs nearly anything can get under the control of the trouble makers if you're not sufficiently cautious and very much secured.
Method 1. With a Spyware
Individuals use spyware applications for different reasons, including parental control of a kid's phone, following a lost gadget, or monitoring worker exercises. MoniMaster Pro has multiple options for android monitoring. You can check your kid's phone on your mobile and take binding actions.

MoniMaster gives a wide range of cell phone observing answers for viable Android, and you don't need to root or escape the objective phone. All practical information can be sent to your nearby PC for the additional survey through MoniMaster. The info you are checking won't ever be hacked or taken for any conceivable explanation.
What Can a Spyware Do?
Spyware can assume command over your gadgets and take your data without you being familiar with it. A portion of the manners it does this is by recording your keystrokes, hacking your camera, or voice calls. It can change your security settings to allow more spyware and produce constant pop-ups.
Features of MoniMaster
MoniMaster Parental Control and family finder' apparatus is intended for occupied guardians. To make them handle their life as a parent is in a lot more straightforward manner. Regardless of where you are at present, how far you are from your kid, and which gadgets your kid and you have - as long as MoniMaster is accessible, your kid is dependable with you.
Messages:
MoniMaster empowers you t view sent and get instant messages along with related documents like photographs without surveying objective phones.
Call History:
Peruse every one of the well known online entertainment discussions and screen the talk history of your children
Child's location:
Keep your kids' area in following inherent GPS and look at every one of the areas chronicles.
View Phone Files:
You can check all contacts, instant messages, photographs, recordings, program history, and introduced applications on the objective gadget with the help of MoniMaster.
Remote Tracking and Control:
They are remotely following the phone areas or setting a protected zone. Likewise, they can catch screen captures, take photographs, and record calls from a distance.
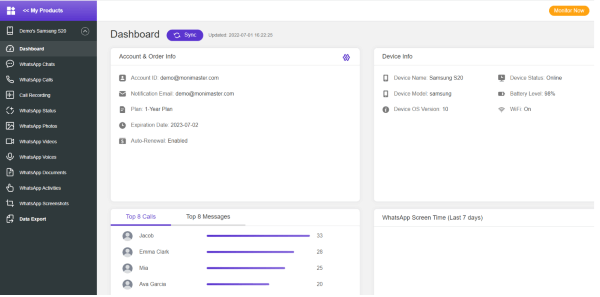
How Does MoniMaster Pro Work?
MoniMaster certifies you to see practically every one of the information on your children's cells without establishing the objective gadget. The web-based information seeing dashboard can guarantee you a 100 per cent secret checking. Follow the below process:
Step 1. Join and Purchase
Utilize your email address to make a substantial record and purchase the arrangement you want. Add your valid details to view the data.
Step 2. Download and Install
Download the app and install it on your phone. Complete the arrangement system, introduce the application, and sign into the record.
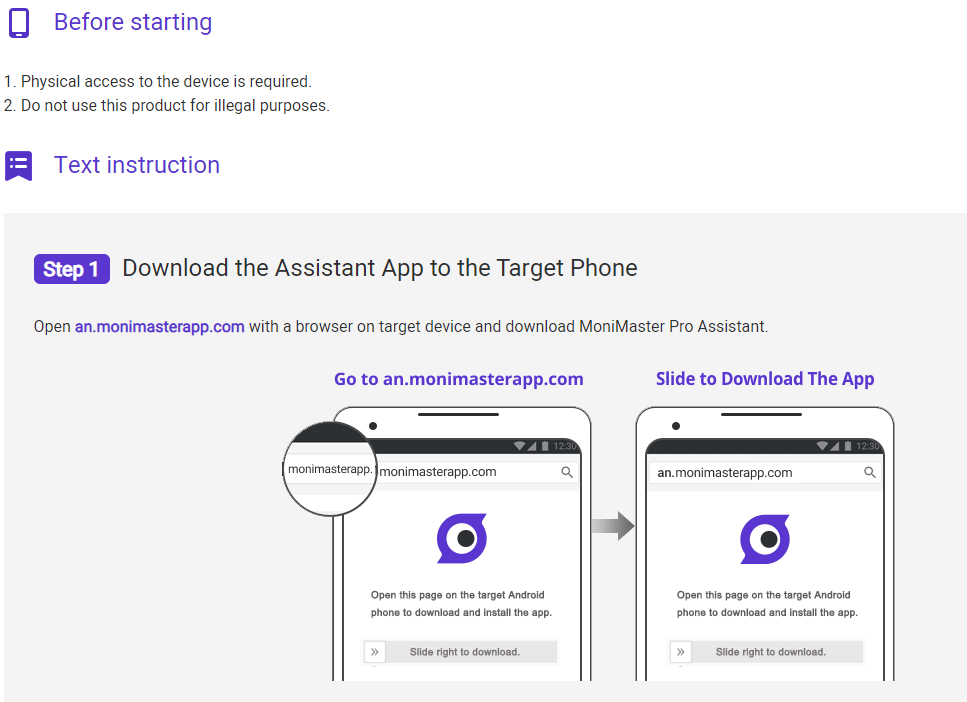
Step 3. Begin Monitoring
After putting the data on the app, go to the observing board on your program to begin checking the objective gadgets.
Method 2. SIM swap attack
Hackers move your phone number to their gadget and get to your record. By utilizing this attack, hackers can carry your phone number to their own SIM card and assume control over your documents.
Method 3. Phishing emails
Hackers email you with a vindictive connection and attempt to fool you into clicking it. Such messages or messages might look genuine. It could be confounded to recognize a pernicious site and a real one: phishing message, Facebook, or email messages with malevolent connections that introduce malware and grab your information.
Method 4. Public Wi-Fi networks
You could get malware through open Wi-Fi organizations or charging stations. Hackers can set up counterfeit Wi-Fi organizations, called fiendish twin organizations, to divert you to vindictive sites or take information using a USB link at a charging station.

Most people find unstable and free Wi-Fi at the closest neighbourhood coffeehouse helpful, not realizing it is also excessively advantageous for hackers. Remember that it is simple for hackers to watch nearly everything you do through Wi-Fi. Accordingly, assuming you should utilize unstable Wi-Fi, guarantee that you also make sure to use a virtual private organization (VPN) because it keeps up with your association's security.
How to Know If Your Phone is Hacked?
Whether you have an iPhone or Android cell phone, some signs demonstrate that your gadget has been hacked. Assuming you notice these things on your cell phone, there may be an opportunity that a cybercriminal has designated you:
- You notice something you don't perceive on your phone (e.g., applications you didn't download, instant messages you didn't send);
- Your Phone works gradually. It utilizes more assets and battery power and becomes more smoking than expected. Malware working behind the scenes could decrease its ability fundamentally;
- Secretive information utilization spikes with practically no progressions on your part. Malignant cycles may be consuming your portable information behind the scenes as they track what you do;
What Can you Do When the Phone is Hacked?
Assume you think that your phone is hacked. You don't have to overreact since you can constantly track down an answer for unexpected issues. Remember that there are five fundamental advances you want to consider to keep you from causing severe harm.
Restoring your device
This whole cycle assists you with cleaning your gadget and reestablishing your information from distributed storage. The strategy can appear attractive, yet it is simpler than you anticipate. Additionally, how you reestablish relies upon your phone model.
Allow multi-factor authentication
Assuming you are concerned because your phone is hacked, you no longer have to stress since you should empower multifaceted verification. Preferably, this is an ideal thought contrasted with trusting that an agreeable gadget will deal with the issue.
Change your essential passwords
It is fitting to change your secret key, all the more so assuming you presume that your phone has been hacked. Although it would be better to avoid it from the gadget that has been hacked, you can utilize another device. Changing the secret key from your hacked phone implies that you would have given the hoodlums your new secret phrase. It means you won't have tackled any issue.
Erase Unknown Applications
The initial phase in safeguarding your phone is to dispose of utilizations you don't recollect downloading. However, remember that some malware can re-download itself, so it's vital to be cautious.
Check your application's approvals
Your contacts, amplifier, and camera can be in every way get to when you introduce applications on your phone. Go to Settings > Manage Applications on your phone to check.
FAQs about Hacking Phone by Calling
1. Can someone hack a phone with just a phone number?
It's vital to emphasize that it's impractical for somebody to sort your number into a few unclear training and snap "HACK". There is generally a course of fooling you into accomplishing something, as referenced previously.
2. How easy is it for someone to hack your phone?
A few alternate ways a programmer can get into your phone include: Through open Wi-Fi organizations. Cybercriminals make counterfeit Wi-Fi organizations, and when you interface with it with your phone, they divert you to malevolent locales. SIM trades. Programmers move your phone number to their gadget and get to your record.
3. Will resetting the phone remove hackers?
Most malware can be eliminated with a plant reset of your phone. It will wipe any information put away on your gadgets, such as photographs, notes, and contacts, so it is vital to back up this information before resetting your device.
4. Can Apple tell me if my phone is hacked?
Whenever Apple recognizes that a client has been designated by state-supported hacking, it will send a message and an email to the addresses on record. Apple said a threat notification would be shown when the client signs into Apple ID.
5. Can I tell if my phone is hacked?
If you find applications you haven't downloaded or calls, messages, and messages you didn't send, that is a warning. A programmer might have captured your phone to send premium-rate calls or news or to spread malware to your contacts. Likewise, assuming you see spikes in your information utilization, that could also indicate a hack.
Conclusion
It is more than unbelievable for hackers to get to your phone using a call, yet allowed an opportunity, they can easily hack your phone. It would help if you realized that hacking could be tricky; however, answering the call can make it easy for crooks to get to your phone. Hence, it is excellent to guarantee that you avoid potential risks constantly. MonoMaster is a handy app for safe and secure monitoring. It will give you 100 per cent best data.
















