Privacy and exposure blur together in an increasingly digital world, and personal and professional data safety is becoming an ever-increasing worry. Questions like, "How to know if someone copied files from my computer?" and "Can you tell if a file has been copied from computer without leaving a trace?" are becoming more frequently heard from individuals concerned.
This article seeks to provide knowledge that equips readers to recognize unauthorized files copied while taking practical measures against breaches and keeping them confidential.

Part 1. The Importance of Computer File Security
Securing computer files is integral in protecting our digital assets and maintaining our autonomy within an ever-evolving digital landscape. This process is essential in preserving various digital files, from personal photos to work documents and confidential communications.
By taking practical security steps, we prevent copied files and potential data breaches and minimize their adverse repercussions. Protecting files copied helps mitigate financial loss, reputational harm, and personal damage.
Part 2. How to Check If Files were Copied from My Computer
Digital or physical security is now essential in today's interconnected world; safeguarding sensitive computer information against unintended access is necessary. Files copied without permission have increased as technology progresses; individuals and organizations alike must employ methods for detecting intrusions into digital assets to detect or prevent them.
1PCSntry: Comprehensive File Monitoring Software Solution
MoniMaster PCSntry is an advanced software solution designed to safeguard against unauthorized access and data breaches on a computer, particularly concerning how to know if someone copied files from my computer. Users will gain access to an extensive suite of surveillance tools designed to keep an eye on computer screen activity on an ongoing basis.
Key Features of MoniMaster PCSntry
File and Software Tracking:
Real-time alerts provide genuine protection from potential data breaches by alerting if there's any unapproved access, changes, copied files, or modification that occurs without authorization - an early line of defense against any data leakages that might otherwise happen.
Social media and Email Monitoring:
Social media and email monitoring services constantly monitor activity across social networks and emails, notifying users if anything suspicious appears that could leak or expose sensitive data.
Screenshot Capture:
Employs an effective strategy by periodically taking screenshots as evidence against any misuse or breach of personal or professional data. This provides tangible proof against unwarranted access or modification.

Keylogger Functionality:
For detection of illegal acts on computers and network services, discreet keyloggers provide invaluable evidence by recording all keystrokes that come across your keyboard - this reveals any content typed onto them, revealing potential criminal acts that occur without your knowledge or approval.
Stealth Mode Operation:
Stealth mode operates covertly in the background to detect malicious actors without their knowing about it, giving a chance for detection in real-time.
How to Check If Someone Copied Files from My PC With MoniMaster
Step 1. Installation and Setup: Begin your PCSntry experience by installing it onto your computer and navigating its user-friendly dashboard to configure settings accordingly.
Step 2. Enabling Screen Monitoring: Enable screenshot capture to start recording screen activities at predetermined intervals - perfect for businesses monitoring employee productivity or individuals concerned about unauthorized access.
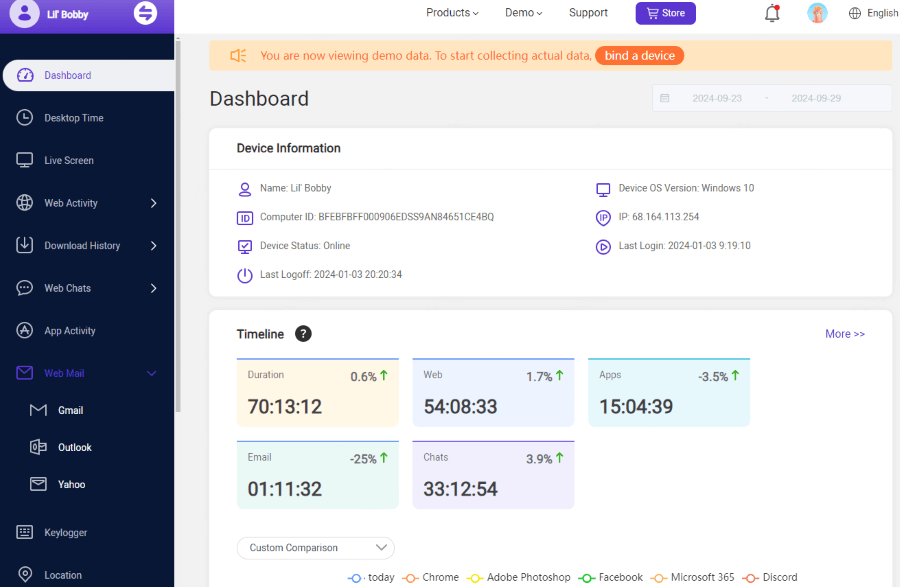
Step 3. Review and Analysis: Regularly review screenshots collected by MoniMaster PCSntry to detect unexpected or illegal activities, such as unknown applications running or files being accessed at odd hours of day or night.
2Check File Access Timestamps
One practical and straightforward method of detecting illegal access to files on your PC is by reviewing their access timestamps - digital footprints that indicate when each file was last opened or accessed and being files copied without your knowledge or consent.
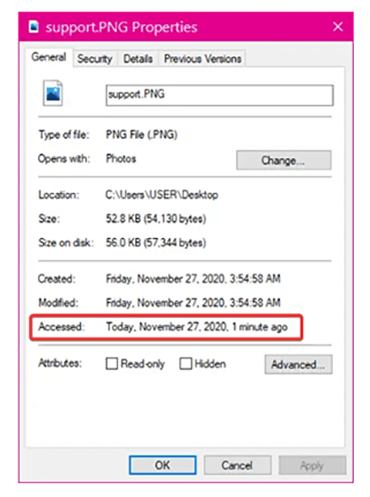
- Timestamp Visibility: Displays the last access time for files directly, clearly indicating when they were last opened or copied by their intended recipients.
- Ease of Use: This approach requires no special tools or software to make it accessible.
- Initial Sign of Intrusion: While inconclusive, unusual access times can serve as a red flag, prompting further investigation.
3Monitor File Modification Dates
Tracking file modification dates can alert you to unwarranted changes that indicate someone is trying to copy files off a computer without leaving trace. This method works because altering any file changes its last modified timestamp and could indicate file theft attempts.
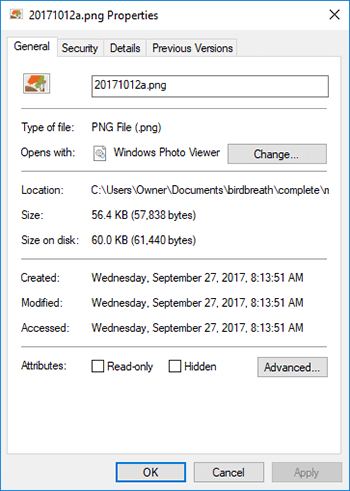
- Modification Date Alerts: Notifying users about file changes that could indicate illegal access or duplication.
- Easy Verification Process: Users can quickly inspect these dates by viewing file properties, efficiently detecting unintended file modifications.
- Unauthorized Alterations Detection: Any discrepancies between these dates could indicate illegal activities like file tampering.
4Review System Logs
System logs provide an invaluable record of actions taken on any computer system. By carefully perusing them, users may discover evidence of files copied without permission - giving insight into unauthorized access or system anomalies that require further investigation.
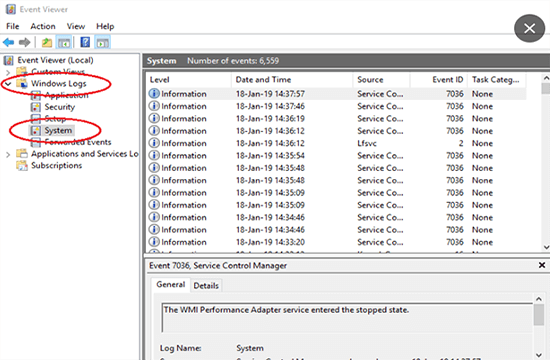
- Detailed Activity Records: System logs provide an in-depth record of every event occurring within your system - from system alerts and warnings to user interactions and more, giving a complete picture of its history and progress.
- Identification of Unauthorized Activity: Specific log entries can reveal attempted unauthorized access attempts, file access patterns, and suspicious activities that require further investigation.
- Technical Knowhow Needed: System logs contain valuable information; however, deciphering them correctly often requires technical savvy.

5Analyze Network Activity
Monitoring data flow on your network is an integral step toward detecting unapproved file transfers that might occur without your knowledge or consent. An unexpected spike in network activity could indicate files are being copied over without permission; using this approach to detect breaches early can prevent further losses or disclosure of sensitive information.

- Traffic Pattern Analysis: Conduct regular assessments of data traffic across your network to detect any irregular activities which could indicate illegal transfers and monitor for potential threats such as viruses.
- In-Depth Connection Monitoring: Monitors inbound and outbound connections to detect suspicious activities involving illicit data transference.
- Alerts on Anomalies: Generate alerts automatically whenever abnormal network activity is identified, enabling quick investigation and response against potential threats.
- Bandwidth Utilization Review: By monitoring how much bandwidth is being utilized versus standard utilization patterns, it's possible to detect significant deviations that indicate data may be being transferred without authorization or may suggest data theft.
6Use File Auditing Tools
File auditing tools are software solutions specifically developed to track all accesses and modifications of files within a system, offering insights on how to know if someone copied files from your computer and thus taking a proactive approach towards data security.
- Automated Monitoring: These tools run continuously in the background to track every interaction with specific files or folders for complete surveillance coverage.
- Alert Notifications: Users receive immediate alerts for unauthorized file activities, enabling quick action against potential security breaches.
- In-Depth Reporting: Generating detailed reports on file access patterns, modifications, and relevant activities provides comprehensive analysis and review for further study and consideration.
- Customization and Control: Allows for tailoring monitoring settings to focus on specific files, directories or activities tailored specifically for individual security requirements.
By employing these strategies, you're taking proactive measures against data breaches or unapproved files copied. Recognizing how to know if someone copied files from my computer is crucial.
Conclusion
Unauthorized access detection and data security protection have been more essential in today's digital world, from monitoring file access timestamps to network activity analysis. MoniMaster PCSntry offers complete protection on how to know if someone copied files from my computer by providing all-encompassing protection of digital assets.

















